Security In Depth
[PDF] Security In Depth Ebook

Network Perimeter Security Building Defense In Depth
Best Security Practices for Azure: Defense in Depth In the previous post of this three-part series, I discussed security practices associated with the Azure sign-up process, role based access controls (RBAC), remote management of your systems in Azure, and network security controls. Now lets build upon the previous post to continue to help create our defense in-depth security posture. Depth Security Information Security Services and Solutions Information Security Solutions. We select solutions and technologies based on their proven effectiveness, not marketing hype. Every technology we recommend includes expert architecture and implementation services. Cloud Security Strategy & Solutions Rackspace Developing a cloud security strategy to protect your IT network is vital to business growth. Rackspace will help define solutions to secure your cloud!
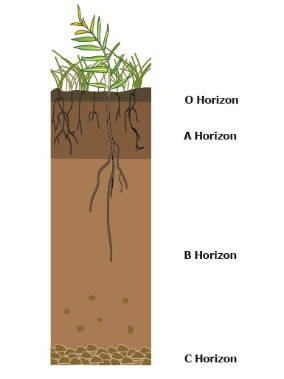
How Soils Form Environment Land And Water Queensland

Mastering R Programming Video Packt Books

The Best Cyber Security Books Out There Chosen By Over 20

Acer Chromebook R11 Cb5 132t C8zw Notebookcheck Net

0 Response to "Security In Depth"
Post a Comment